TryHackMe - Basic Malware RE
Greetings, fellow tech enthusiasts and security adventurers! This blog chronicles my journey into the cryptic world of malware analysis and reverse engineering. Buckle up, because I’m starting as a (maybe not so) complete n00b, determined to navigate the complexities of this domain.
In our inaugural post, we dive straight into the action with a focus on challenges from TryHackMe’s Basic Malware RE (Reverse Engineering). Join us as we navigate through real-world scenarios, dissecting malware samples, and uncovering the tactics used by cybercriminals to evade detection and wreak havoc (that’s what they do, right?).
Consider this a real-time learning experience, where I’ll be sharing my struggles, breakthroughs, and hopefully, some valuable insights along the way. Resources, technical breakdowns, and the occasional head-scratching moment - you’ll find it all here.

Strings :: Challenge 1:
Alright folks, let’s dive into the first challenge of TryHackMe’s Basic Malware RE course!
Step 1:
Initially, I went down the route of using a tool called PEStudio to extract all the strings from the provided binary. This seemed like a straightforward approach, but PEStudio picked up a lot of “false flags” prepared to distract any approaching analyst. This was a real rabbit hole, sending you down paths that ultimately lead nowhere.
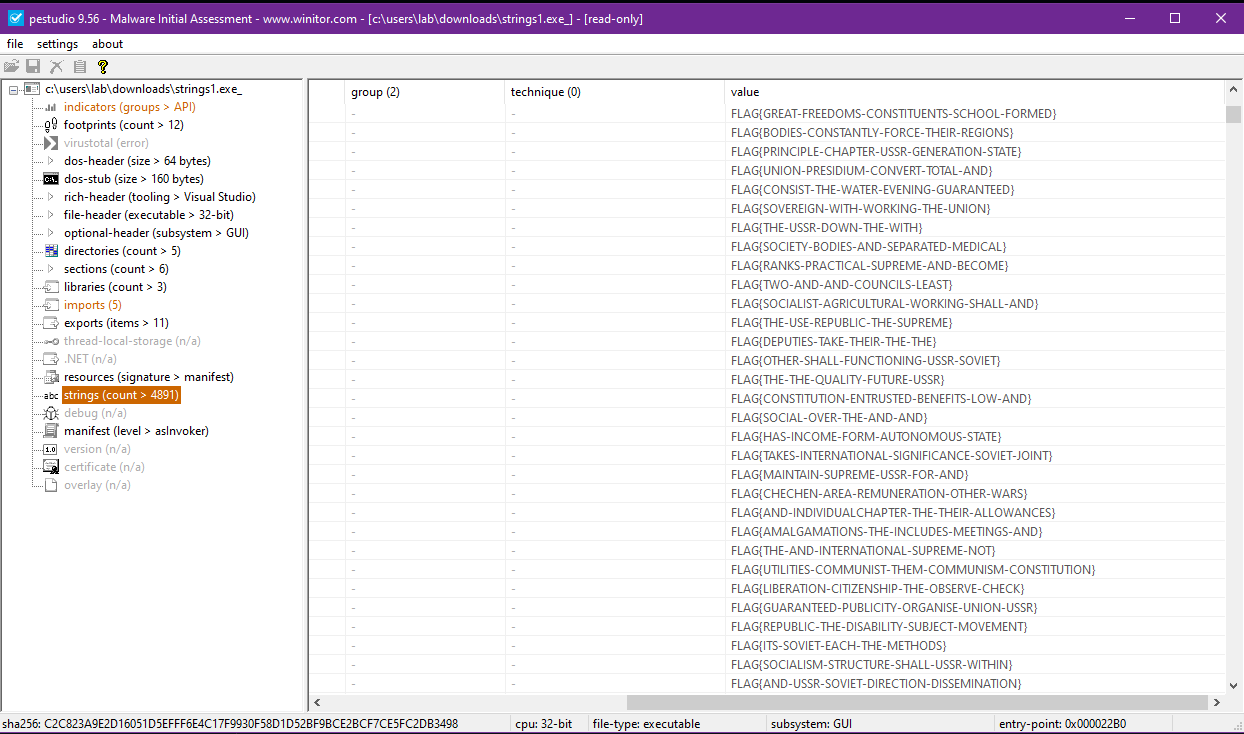
Step 2:
Realizing this, I switched gears and fired up Ghidra (while loving NSA as much as I love taxes). Navigating through the code, I have easly identified the program’s entry point. Following the execution flow from the entry point led me to the actual flag referenced on the screen:
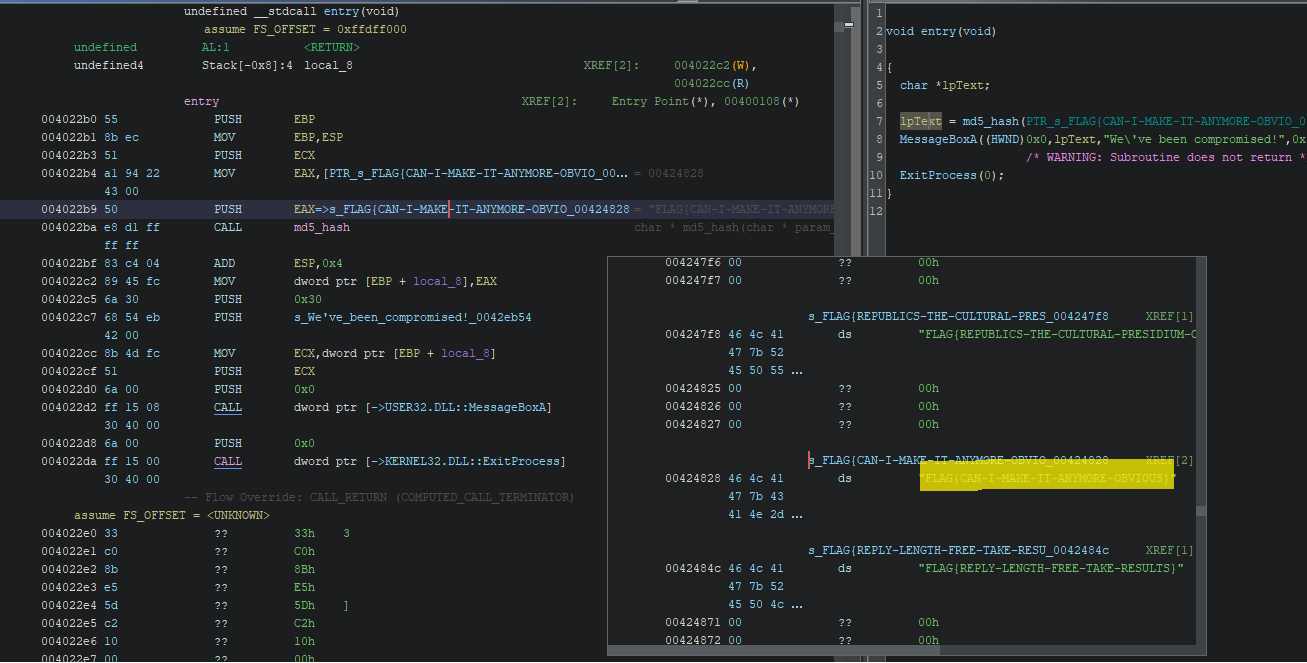
Strings :: Challenge 2:
Step 1:
After anlysing entry function, it appears we have several variables in a stack represented by hexadecimal (hex) values, which are being hashed sequentially to form the final string. By converting these hex values into ASCII, we should be able to identify the values contributing to the flag.
Step 2:
Simple Python script to concatenate values into flag (this is not production-ready enterprise code, as You see).
with open('strings2.txt', 'r') as stringsFile:
for line in stringsFile:
print(line.strip()[-2], end = '')
Strings :: Challenge 3:
Step 1:
String extraction wasn't enough, so BinText was used for faster results than PEStudio.
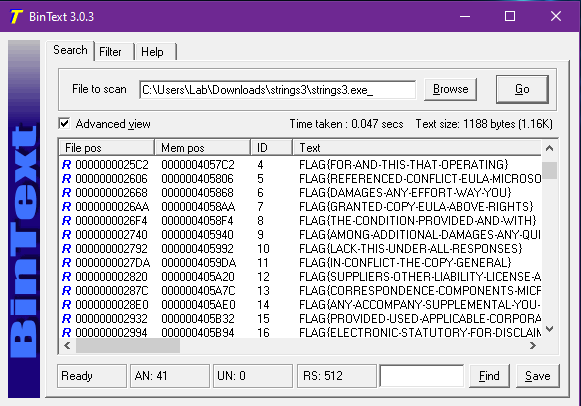
Step 2:
We need to examine dissasembled code. First step will be understanding entry function and further logic flow.
We can notice that Ghidra is already shoing us the correct flag:
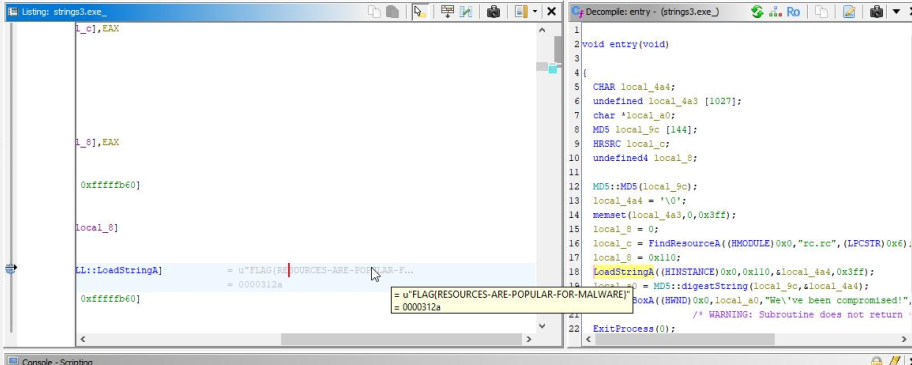 But we can also find it manually, following LoadStringA function, and its uID parameter, pointing at 0x110 (String ID -> 272 in decimal).
But we can also find it manually, following LoadStringA function, and its uID parameter, pointing at 0x110 (String ID -> 272 in decimal).
