Practical Malware Analysis - Labs Writeup - Lab 1
In this blog posts series, I’ll be delving into the practical exercises provided in the renowned book “Practical Malware Analysis,” offering insights, strategies, and hands-on experiences to fortify my understanding of malware behavior and analysis techniques.
I will also try out more modern tools and prepare things like Yara rules and more extensive reportes whenever possible, in order to use every opportunity to sharpen all those essential and additional skills.

[!NOTE] Post is still work in progress.
Chapter 1
Lab 1-1:
Hashes:
dll:
MD5: 290934c61de9176ad682ffdd65f0a669
SHA1: A4B35DE71CA20FE776DC72D12FB2886736F43C22
SHA256: f50e42c8dfaab649bde0398867e930b86c2a599e8db83b8260393082268f2dba
exe:
MD5: bb7425b82141a1c0f7d60e5106676bb1
SHA1: 9dce39ac1bd36d877fdb0025ee88fdaff0627cdb
SHA256: 58898bd42c5bd3bf9b1389f0eee5b39cd59180e8370eb9ea838a0b327bd6fe47
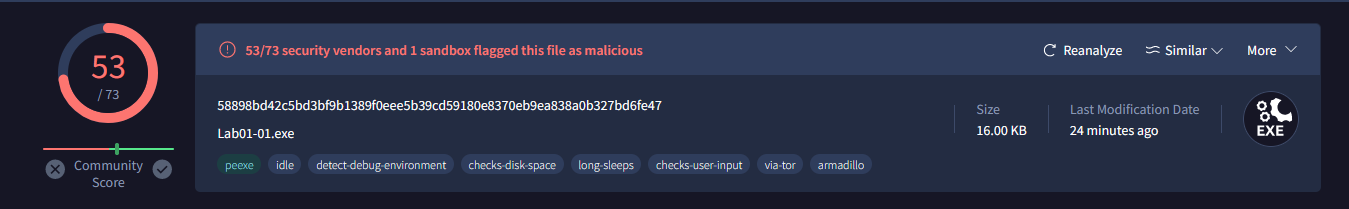
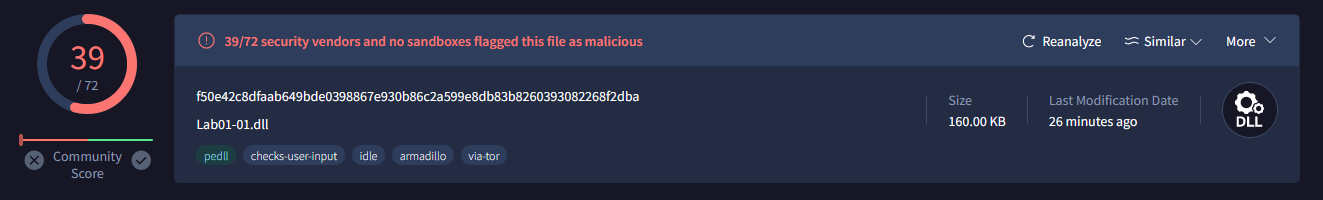
Question 1: Upload the files to http://www.VirusTotal.com/ and view the reports. Does either file match any existing antivirus signatures?
Lab01-01.exe
Lab01-01.dll
Question 2: When were these files compiled?
Lab01-01.exe
| Sun Dec 19 16:16:19 2010 | UTC |
Lab01-01.dll
| Sun Dec 19 16:16:38 2010 | UTC |
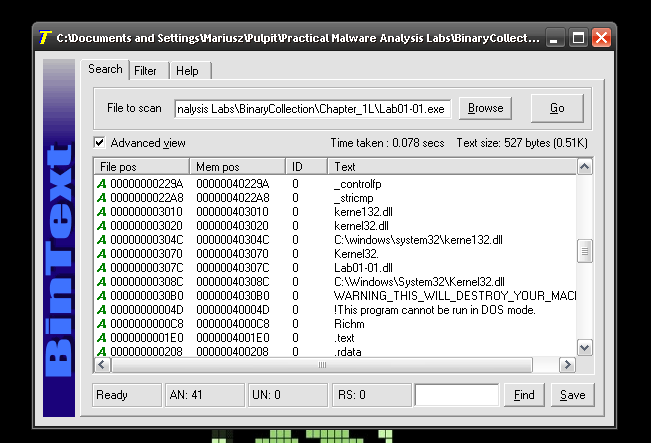
Question 3: Are there any indications that either of these files is packed or obfuscated? If so, what are these indicators?
Lab01-01.exe

Lab01-01.dll
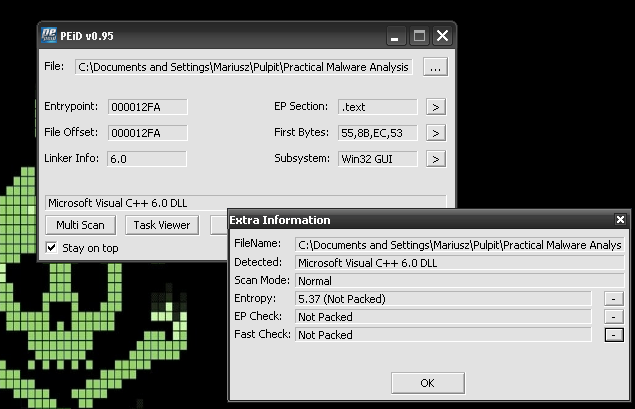
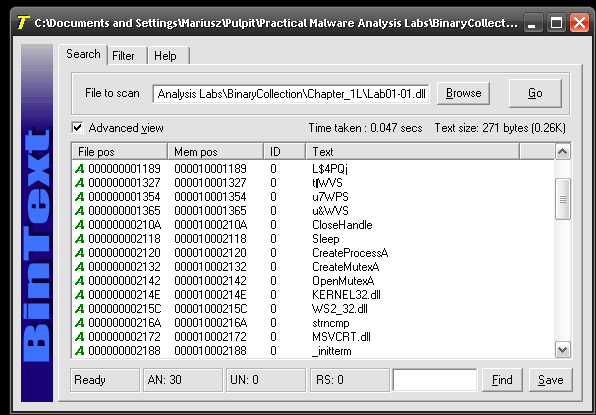
For both samples calculated entropy is in the mid range, PEiD didn’t detect any packer used, but was able to detect most likely used compiler. BinText we are able to see readable strings. So there are no indicators that those binaries were packed.
Question 4: Do any imports hint at what this malware does? If so, which imports are they?
For Lab01-01.exe there are a couple of imports that attract attention:
- -KERNEL32.dll
- → CopyFileA / CreateFileA / CreateFileMappingA
- → FindClose / FindFirstFileA / FindNextFileA
- → IsBadReadPtr
- → MapViewOfFile / UnmapViewOfFile
Potentially the binary creates some files. Potential dropper (?)
Lab01-01.dll:
- -KERNEL32.dll
- → CreateProcessA
- → Sleep
Most likely this dll spawns a new process, and some of its actions are delayed (maybe to make malware less likely to be noticed by the user? Or to synchronize its activity with some events/resource availability?).
There are also imports from WS2_32.DLL called by ordinal. And all of them suggest some kind of network activity being involved.
- → socket
- → WSAStartup
- → inet addr
- → connect
- → send
- → shutdown
- → recv
- → closesocket
- → WSACleanup
- → htons
Question 5: Are there any other files or host-based indicators that you could look for on infected systems?
In String of Lab01-01.exe we can find reference to file kerne132.exe (with “one” instead of L) in location C:\windows\system32.
For Lab01-01.dll there is no indicators.
Question 6: What network-based indicators could be used to find this malware on infected machines?
Lab01-01.exe doesn’t contain any obvious network related indicators.
Lab01-01.dll references ip address of 127.26.152.13.
Question 7: What would you guess is the purpose of these files?
RAT/backdoor disguised as a system file (kerne132.dll), with persistance implemented.
Lab 1-2:
Hashes (Packed):
MD5: 8363436878404da0ae3e46991e355b83
SHA1: 5a016facbcb77e2009a01ea5c67b39af209c3fcb
SHA256: 1c876a332d7dd8da331cb8eee7ab7bf32752834d4b2b54eaa362674a2a48f64a61
Hashes (Unpacked):
MD5: 8363436878404da0ae3e46991e355b83
SHA1: 5a016facbcb77e2009a01ea5c67b39af209c3fcb
SHA256: 1c876a332d7dd8da331cb8eee7ab7bf32752834d4b2b54eaa362674a2a48f64a61
Question 1: Upload the Lab01-02.exe file to VirusTotal. Does it match any existing antivirus definitions?
This sample is old, so nothing suprising there.
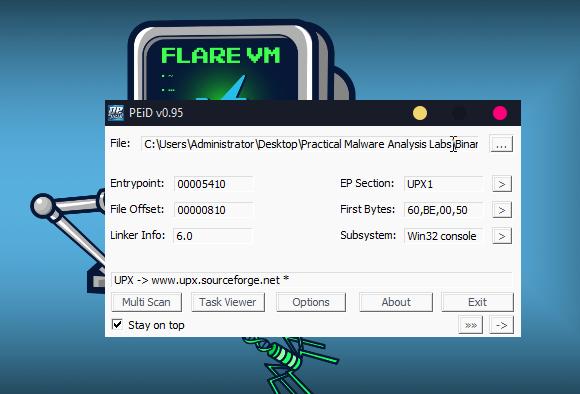
Question 2: Are there any indications that this file is packed or obfuscated? If so, what are these indicators? If the file is packed, unpack it if possible.
With PEiD we can quickly find that it detects that UPX packer was used and entry point -> UPX1.
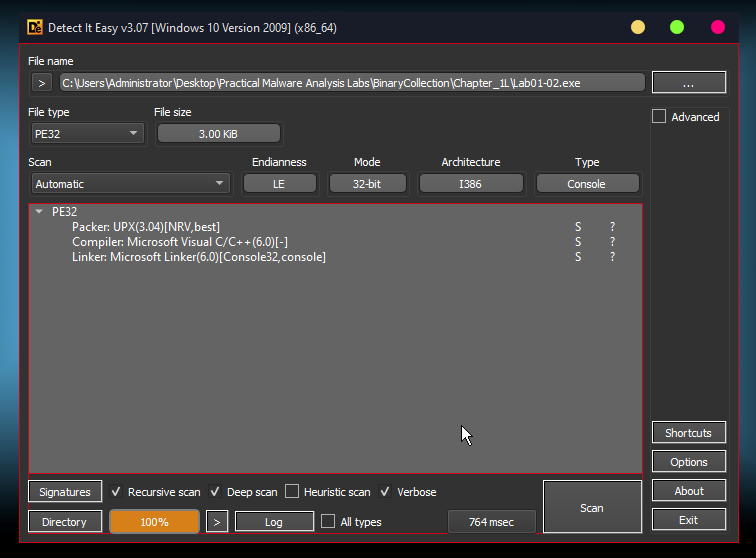
We get same result with Detect It Easy:
String extraction also confirms that UPX was used:
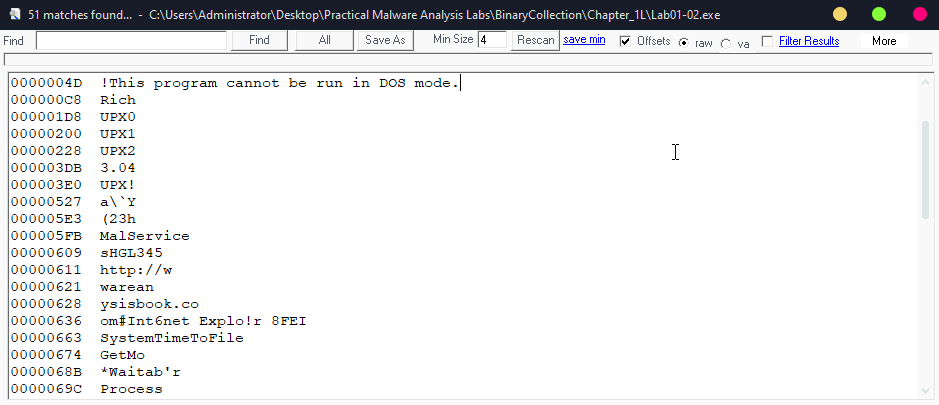
TODO: Try to perform manual unpacking!
Question 3: Do any imports hint at this program’s functionality? If so, which imports are they and what do they tell you?
Lab01-02.exe -> Packed:
- -KERNEL32.dll
- → VirtualProtect
- → VirtualAlloc
- → VirtualFree
- → ExitProcess
- → LoadLibraryA
- → GetProcAddress
- -ADVAPI32.dll
- → CreateServiceA
- -WININET.dll
- → InternetOpenA
Lab01-02.exe -> Unpacked:
- -WININET.dll
- → InternetOpenA
- → InternetOpenUrlA
- -ADVAPI32.dll
- → CreateServiceA
- → StartServiceCtrlDispatcherA
- → OpenSCManagerA
- -KERNEL32.dll
- → SystemTimeToFileTime
- → GetModuleFileNameA
- → CreateWaitableTimerA
- → ExitProcess
- → OpenMutexA
- → SetWaitableTimer
- → WaitForSingleObject
- → CreateMutexA
- → CreateThread
InternetOpenA + InternetOpenUrlA:
Internet-related functions
→ Some kind of internet connectivity. Connection to C2 server?
→ Download additional binaries/resources (?)
CreateServiceA + StartServiceCtrlDispatcherA + OpenSCManagerA:
Service management function
→ Most likely persistance utilising Windows Service.
CreateMutexA + OpenMutexA + (CreateThread):
→ Enforce single instance of process, possibly in a new thread.
SystemTimeToFileTime + CreateWaitableTimerA + WaitForSingleObject:
→ Some time sensitive functionality. Possibly scheduled request to C2?
Question 4: What host- or network-based indicators could be used to identify this malware on infected machines?
Host based: MalService (?)
Network based: There is a reference to URL: hxxp[://]www[.]malwareanalysisbook[.]com/ that might potentialy be used for C2 connection.
Lab 1-3:
Hashes:
MD5: 9c5c27494c28ed0b14853b346b113145
SHA1: 290ab6f431f46547db2628c494ce615d6061ceb8
SHA256: 7983a582939924c70e3da2da80fd3352ebc90de7b8c4c427d484ff4f050f0aec
Question 1: Upload the Lab01-03.exe file to VirusTotal. Does it match any existing antivirus definitions?
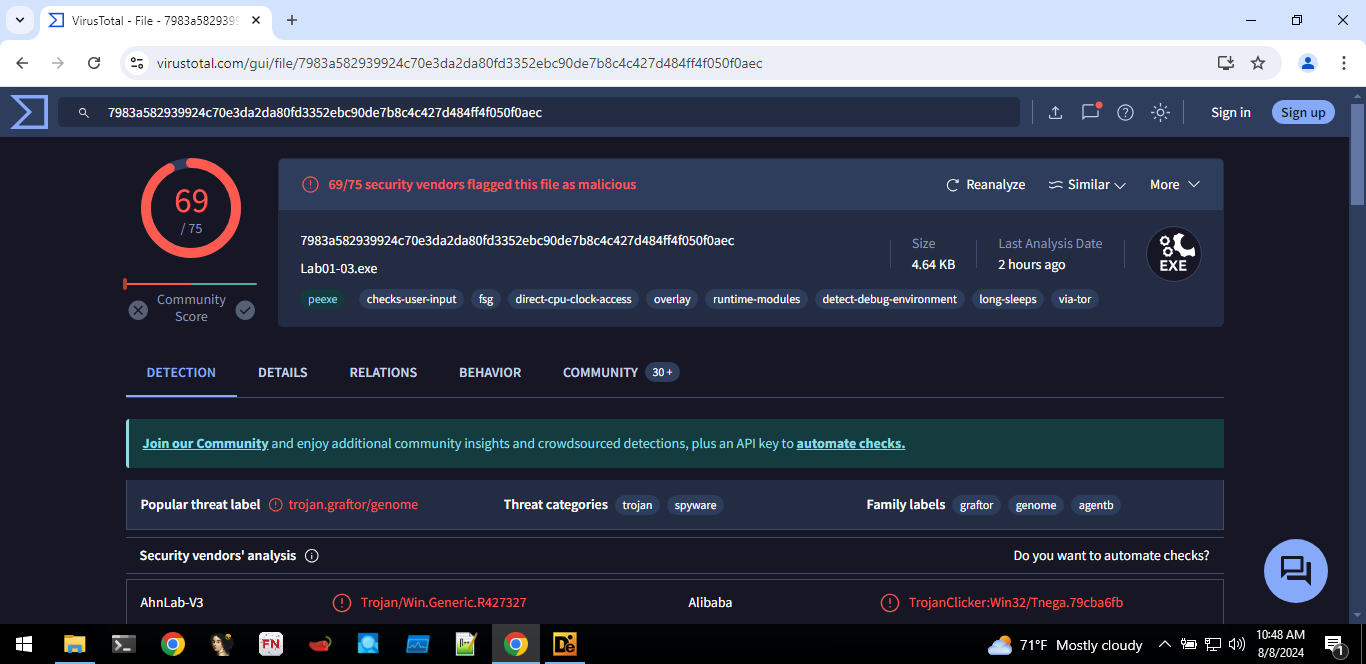
Question 2: Are there any indications that this file is packed or obfuscated? If so, what are these indicators? If the file is packed, unpack it if possible.
When we check the binary with PEiD, tool suggests that the file is packed with FSG 1.0 -> dulek/xt.
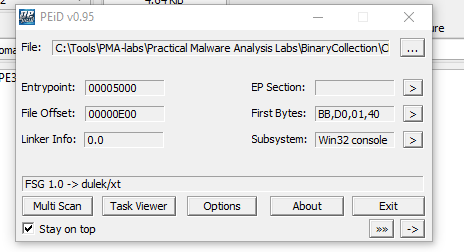
String extraction only revealed small amount of meaningful strings, while imports table consists of LoadLibraryA and GetProcAddress from KERNEL32.dll (those two are required to call unpacking logic).
Additionaly Entropy is equal to 7.351.
Question 3: Do any imports hint at this program’s functionality? If so, which imports are they and what do they tell you?
We cannot say anything without unpacking the sample first.
Question 4: What host- or network-based indicators could be used to identify this malware on infected machines?
Nothing can be extracted from unpacked sample.
Lab 1-4:
Hashes:
MD5: 625ac05fd47adc3c63700c3b30de79ab
SHA1: 9369d80106dd245938996e245340a3c6f17587fe
SHA256: 0fa1498340fca6c562cfa389ad3e93395f44c72fd128d7ba08579a69aaf3b126
Question 1: Upload the Lab01-04.exe file to http://www.VirusTotal.com/. Does it match any existing antivirus definitions?
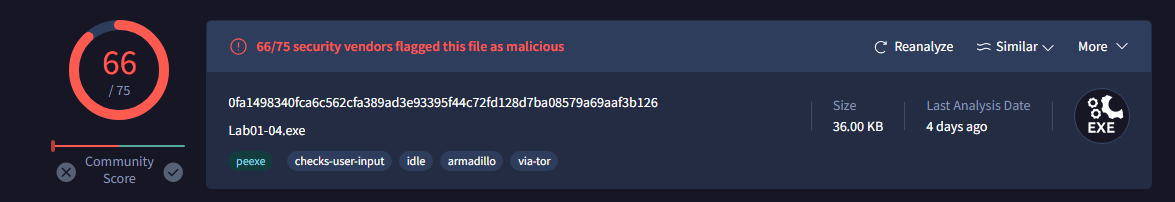
Question 2: Are there any indications that this file is packed or obfuscated? If so, what are these indicators? If the file is packed, unpack it if possible.
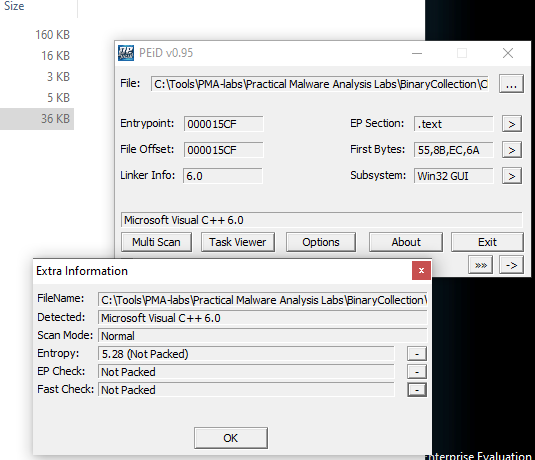
Based on results from PEiD binary is not packed, with entropy equal to 5.28:
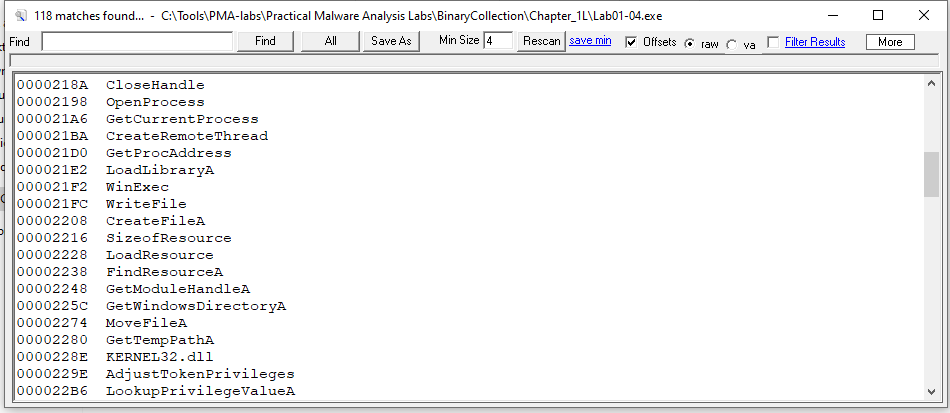
Strings are also human-readable, that strongly suggests that the sample is not obfuscated:
Question 3: When was this program compiled?

